hmc
Active Member
Hi guys,
my libiconv problem is driving me nuts!
I'd kindly ask someone with some time on his hands and with decent PND knowledge to assist me sorting that out.
Situation is as follows:
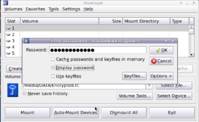
My TrueCrypt PNDcontains a folder "lib", which contains libiconv.so.2.
The run script of the PND contains the code
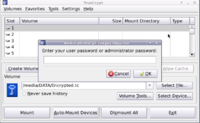
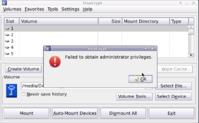
But when I attempt to mount a TrueCrypt container, after entering the container password and then the user password, TrueCrypt claims that "libiconv.so.2" is not available!
I think this is a new problem in SuperZaxxon release 1.5. I think that in SuperZaxxon Beta5 this has worked. but I am not 100% sure about that.
Could anyone please help me? I am stuck with that problem now. :-(
Helping me would mean
- downloading the PND
- creating a truecrypt container to test with
- reproducing the error
- disassembling the PND
- analyzing the reason for the problem
This would be really great.
Thank you in advance!
Daniel
my libiconv problem is driving me nuts!
I'd kindly ask someone with some time on his hands and with decent PND knowledge to assist me sorting that out.
Situation is as follows:
My TrueCrypt PNDcontains a folder "lib", which contains libiconv.so.2.
The run script of the PND contains the code
Code:
LD_LIBRARY_PATH="./lib"
export LD_LIBRARY_PATHBut when I attempt to mount a TrueCrypt container, after entering the container password and then the user password, TrueCrypt claims that "libiconv.so.2" is not available!
I think this is a new problem in SuperZaxxon release 1.5. I think that in SuperZaxxon Beta5 this has worked. but I am not 100% sure about that.
Could anyone please help me? I am stuck with that problem now. :-(
Helping me would mean
- downloading the PND
- creating a truecrypt container to test with
- reproducing the error
- disassembling the PND
- analyzing the reason for the problem
This would be really great.
Thank you in advance!
Daniel
Last edited by a moderator: