kuru
Sadly, again: Je suis Charlie
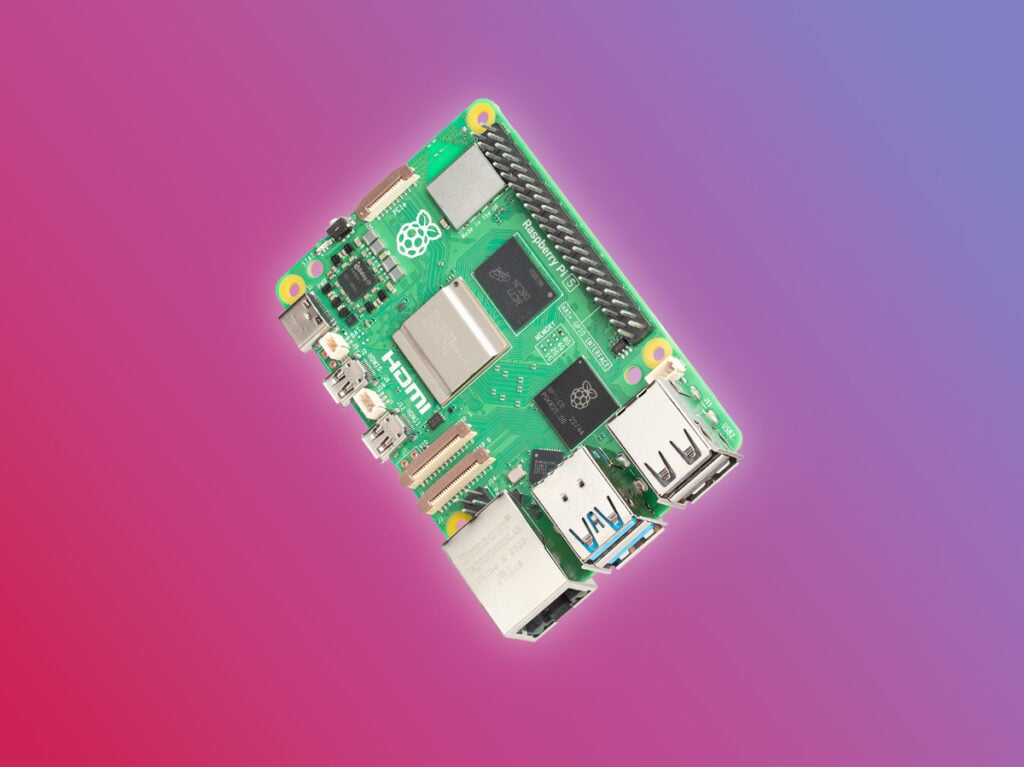
Introducing: Raspberry Pi 5! - Raspberry Pi
Announcing Raspberry Pi 5, coming in late October: over 2x faster than Raspberry Pi 4, featuring silicon designed in-house at Raspberry Pi.
- 2.4GHz quad-core 64-bit Arm Cortex-A76 CPU
- VideoCore VII GPU @ 800 MHz, supporting OpenGL ES 3.1, Vulkan 1.2 - with open source drivers waiting to be released
- 4Kp60 HEVC decoder but it does NOT support H264 hardware decoding. Software decode will bind CPU resources and use quite some power
- Dual-band 802.11ac Wi-Fi®
- Bluetooth 5.0 / Bluetooth Low Energy (BLE)
- High-speed microSD card interface with SDR104 mode support
- 2 × USB 3.0 ports, supporting simultaneous 5Gbps operation
- 2 × USB 2.0 ports
- Gigabit Ethernet, with PoE+ support (requires separate PoE+ HAT, coming soon)
- 2 × 4-lane MIPI camera/display transceivers
- PCIe 2.0 x1 interface for fast peripherals
- Raspberry Pi standard 40-pin GPIO header
- Real-time clock
- Power button
- The RP1-Chip is an in-house development that has been going on since 2015 and cost over 10.000.000 $. It has 16 Gbps bandwidth and handles all the I/O - including a PCIe slot, for which an M.2 HAT will be made available. The RP1 allows both USB 3.0 to run at full 5Gbps, and both USB 2.0 to run at 480 Mbps. SD card speeds have about doubled in comparison to RasPi 4.
- The MIPI connectors allow connecting either two displays, two cameras, or a mix. Out-of-the-box stereo vision!
- The 3,5 mm headphone jack had to go.
- There are two thru-hole solder points for video out.
- There is a dedicated 3-pin fan connector.
- The power button allows for a clean shutdown.
- Typical power consumption ranges between 3.3 and 8.6 watts. A few sources report spikes up to ~12 amps. A power-delivery-enabled supply capable of 5 V, 5 A will be sold for the Pi 5. EDIT: Apparently the old 3 A power supply can still be used. In that case the USB slots' available current will be limited to 0,6 instead of 1,2 amps.
Release date is late October, price for the 8 GB model is about 80 $, and 60 $ for 4 GB. That is before the scalpers get their grubby mitts on them.
1 and 2 GB versions might become available later.
A few videos in the spoiler.
Chris from explainingcomputers
Jeff Geerling
David Bombal incl. interview with Eben Upton
c't 3003 (deutsch)
NetworkChuck
Jeff Geerling
David Bombal incl. interview with Eben Upton
c't 3003 (deutsch)
NetworkChuck
I was so close to pulling the trigger on an Orange Pi last night. Glad I slept over it, this is fantastic news. Support and documentation will be so much better for the RPi. And it's mostly made in Britain.
If you find more interesting information, written reviews or videos, post below and I'll add it here.
Last edited:

